Shirt Pocket
Snapshot Surprise! Friday, December 08, 2017
We've got something under the tree for all of you, and you get to open your present early.
Executive Summary
SuperDuper! 3.1 is out, and now allows Time Machine-like restoration from bootable APFS copies.
Wait, What?!?!
Oh, decided to join us for the details? Welcome to an ocean of words: prepare to get your feet wet!
Well, I told you there would be more surprises in store, and, so, here we are. Since the release of 3.0, we've not only been copying from a snapshot when using an APFS source. In addition, as some of you have noticed, we've also been creating snapshots on the backup.
This is why.
Turn Back the Clock
In SuperDuper! v3.1, you may notice a small change to the Copy Now button: a little up-triangle glyph. If you've selected an APFS volume as your source, you can click that triangle, and up pops a list of the snapshots available to copy from.
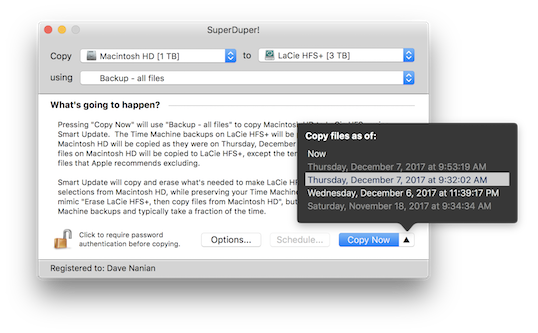
This means you don't just have to copy from the drive as it is "now" (the default choice). You can select from any existing snapshot, and we'll copy the state of the files as they were at that time.
But why would you want to do that?
Well, in High Sierra, the system takes a snapshot of your drive before it installs a software update. Having a problem with an update and want to check if it was different before, but forgot to back up first? No problem: use SuperDuper! to copy from the snapshot taken just before the update was installed, start up from the copy, and check the behavior.
Even better, if you're backing up to an APFS volume as we encourage, this works on a bootable copy, too! Since v3.0, we've been taking a snapshot of the backup volume before every copy we make. That means there's not just one available backup on the drive—if you've been using Smart Update, there are many! Start up from your backup drive, click the triangle, and you'll be presented with a list of available snapshots. Pick one, "Copy Now", and you've restored a day ago's backup, or a week ago's.
But Wait—There's More!
In fact, not only can you use SuperDuper to copy from these snapshots, you can even open Time Machine, select your backup volume, and see older versions of files, deleted files - they're all being saved, automatically, every time you Smart Update. Even though you're not backing up your backup to Time Machine. Because that would be silly.
This new feature is not intended to replace or replicate what Time Machine does. Snapshots are managed by the system, and at present they have some lightly-to-not documented constraints. You need to have about 20% free in a container to create a snapshot, and the system consolidates and removes snapshots according to its own logic.
As I've said before, an effective backup strategy should have multiple parts: SuperDuper!, Time Machine and an online service. The more (and more varied) backups you have, the safer you are. This new feature gives SuperDuper!'s bootable backups some cool new capabilities and an additional measure of protection should you make a mistake.
Now How Much Would You Pay?
Pretty awesome, right?
Needless to say, this is the kind of feature we love to introduce. It's completely transparent to the user, and is built on the extensive work we did to support APFS in v3.0. That support wasn't done at a surface level: we worked hard to research and make use of the more advanced features, like snapshots, and planned for the future in ways that truly make the backup experience better for everyone.
Including you. Update away!
Download SuperDuper! v3.1
It’s Not a Turkey Monday, November 20, 2017
One of the weird parts of doing a public beta, as we did for 3.0, is that the release of the final version doesn't quite feel the same. So, even though it's only been two weeks since 3.0 came out...it feels like it was released months ago.
The 3.0 release has actually gone incredibly smoothly. The extended beta managed to attract a large number of diverse system configurations, and that helped us ensure that any post-release issues would be...obscure. And, indeed, they have been!
Pulling the Right Levers
A program like SuperDuper! needs to make choices about how to interface with the system. There are many different layers, and we try to choose appropriately, depending on what we're doing.
To ensure a maximum level of compatibility, it's incredibly important to work at as high a level as possible for any given activity. For example, when SuperDuper! needs to erase a drive, it would be a huge mistake to actually jump down to the driver level and start mucking with drive structures.
Instead, we do the sensible thing: we ask Disk Utility to do it for us.
Talk to the Command
Disk Utility, though, is what's called a command-line tool: you can run it yourself, from the Terminal application, if you want to: type diskutil to see what it does, and man diskutil for its documentation. Much of macOS is built upon these Unix tools, and (where appropriate), so is some of SuperDuper.
When you talk to a tool like this, though, you have to both check its "return value" (basically, a rough "I worked!" or "I failed!"), and its text output (which says why it worked or failed, or gives you an answer to a question you asked).
Some of these tools (diskutil, hdiutil, etc) will format their output in plist format: basically, a structured XML document that's far more predictable, easier to parse, and more reliable. So rather than returning "Drive formatted as HFS+", it might return (intentionally simplified)
<format>hfs+</format>
which is obviously less friendly to people, but a lot better for programs trying to figure out what's going on.
This plist output's advantage is that its structure is strictly defined. It has a prologue, a series of tags and values, and an end. This is all guaranteed.
Samsung!
So, when a few users started getting some crazy, inexplicable errors (typically, an error indicating that a volume that was there couldn't be accessed), we were shocked to find, after doing some extensive investigation, that a Samsung SMART driver (based on an open source project) was actually polluting diskutil's output with a bunch of debugging/progress junk.
Needless to say, this prevented parsing of the output, and resulted in a stream of invective that did not diminish for many minutes. So frustrating. But fixed.
Various Improvements
That was the big one. But we also fixed a number of other things:
Finally fixed the update animation bug! So, if you install 3.0.1, the next release is going to show up properly in all cases. This time for sure!
This took such a long time to fix because it was entirely timing related and didn't happen in the debugger. But, we figured it out. So embarrassing. Gonna miss you, you little rascal. (Please don't darken our UI door ever again.)
- Settings conversion related quit issues
- More reliable sleep prevention during a copy
- Supports encrypted destination volumes on 10.12
- Restored 10.9 support
I also took some time over the past week to turn on SSL for Shirt Pocket, so site access and downloads are all being done securely.
Happy Thanksgiving
So, with that, from our families to yours, have a Happy Thanksgiving, and enjoy SuperDuper! 3.0.1, which is available via the built-in updater, from the web site, or here:
SuperDuper! 3.0.1 Download
Bad Craziness, Good Release! Wednesday, November 08, 2017
The short version
Blah-blah-blah what-the-heck-are-you-talking-about-Dave so many words oh, 3.0 is released? Got it.
The wordy-but-interesting version
Sometimes, on macOS, you run into behavior that really makes you go "huh".
An example: as you likely know, you can create a disk image with Disk Utility and format it as APFS. Which works fine.
And, if you've been reading the blog, you probably also know that APFS volumes reside in a container, which itself resides on a GUID partitioned drive. So, multiple layers: drive, partition, container, volume. You can see all those in Disk Utility.
But once you create the image, what you see in Finder is simpler: a single ejectable volume, with the name you gave it. So, you can open it, copy to it, eject it, and there you go.
Great, right?
Not so much
Ah, but programmatically, things are different.
If an application opens an image the old way, and then unmounts its volume using diskutil, umount or hdiutil, it doesn't do what it used to do.
You can easily see this in Disk Utility, too. After you create the image, try selecting the volume and clicking the eject button. When you do that, you'll see that while the volume ejected, the image is still sticking around in the sidebar. And if the image is hosted on an ejectable drive or network volume, and you then try to eject the host volume, you'll find the it can't be ejected.
Worse, if you force eject the host at this point (hey, folks—don't force eject!), you can damage the image.
Not good.
Huh.
Worlds within worlds
So, what's going on is that there are still two things "attached" from the image: the container and the partition. They don't get "released" after all the volumes are ejected for some inexplicable reason. And so, any application that mounted and ejected images can no longer rely on the previous behavior.
Mischief, managed
Fortunately, this is another situation that SuperDuper! handles for you. If you back up to an image file, you don't need to know what I've just explained: we deal with the details, and eject all the "parts" of an APFS image without any manual intervention.
As you've heard many times from me: it just works.
So while you may not want to know why, or how all this is accomplished...isn't it comforting to know that someone's figured it out and has your back?
#Finally
With that last bit of explanation, I'm happy to say that we've reached the end of this particular voyage. SuperDuper! 3.0 (release 100!) is done, and you'll find the download in the normal places, as well as in the built-in updater, for both Beta and Regular users.
SuperDuper! 3.0 has, literally, many hundreds of changes under the hood to support APFS, High Sierra and all versions of macOS from 10.9 to the present.
SuperDuper! 3.0 is the first bootable backup application to support snapshot copying on APFS, which provides an incredible extra level of safety, security and accuracy when backing up. It's super cool, entirely supported (after all, it's what Time Machine uses...and it was first overall), and totally transparent to the user.
It doesn't stop there, of course. We're already in progress on the next version, and we've got some really great things planned.
Thanks to all of you who participated in the beta, because the final release couldn't have happened without you.
And to those of you who didn't participate in the Beta: you are going to love the final result.
Without further ado, download SuperDuper! 3.0
Enjoy!
The Beta 7 Spooktacular! Wednesday, November 01, 2017
Gee, do you think the original plan was to release this update on Halloween? Spoooooky!
Poof!
When “Erase, then copy” is selected, SuperDuper! has always endeavored to match the format of the source. That is, if the source is Mac OS Extended [HFS+] (Journaled), and the destination is Mac OS Extended (Case Sensitive), on an erase, the destination would end up matching the source, adding Journaling and removing Case Sensitivity.
As I mentioned in one of my first High Sierra posts, we always knew this wouldn’t work when going HFS+ to APFS: you just can’t format an APFS container as HFS+ safely, since it can affect more than just the one volume.
We’ve discovered during our broader Beta rollout that, due to weird bugs in Disk Utility, formatting an HFS+ drive as APFS is unreliable too. Sometimes the drive just “vanishes” and doesn’t re-mount. Sometimes it fails for no reason. Sometimes it makes the one volume unreadable until it’s erased again.
It’s kind of scary crazy. But that seems to be par for the early version High Sierra course. It’s relatively solid in the main, but really weak at the margins.
...But I Don’t Do That
So, we’ve made a change in our “magic” behavior to deal with these issues. Basically, we continue to do what we’ve always done. But if the “major” part of the file system doesn’t match (that is, HFS+ and APFS), we just maintain the existing format of the drive.
So, if you copy APFS to an HFS+ volume with erase, we’ll erase the destination but leave it as HFS+.
Hopefully we’ll be able to change this as macOS stabilizes further.
Enter the Void
I regret to say that we’ve fixed the “black flash” bug, so you’ll no longer have a moment to stare into the blackness as it stares back at you.
Perhaps that’s for the best.
Spaced
We didn't notice (but should have) that our various numbers were now proportionally spaced rather than monospaced since we built against a newer SDK with different targeting when we made the UI 64-bit.
Of course, someone—and you know who you are—noticed right away. Embarrassing, and fixed.
It’s Log, It’s Log!
One of the things we’ve done is improve our diagnostic logging, so when people send in a bug report, we get a better feeling for the state of the drives attached to the system, and the problems that might be going on with the system, should there be any.
We changed this a bit to only collect the extended log information when copies fail.
In earlier OS versions we would include a bit of the system log, so we could see what hardware was doing at the time of the copy. That stopped working in recent macOS release, so we've changed it to use log show.
The problem is, log show -last 1m, including a kernel predicate so it only returns low-level kernel logging, can be slow. Not only that, but due to bugs in the logging subsystem, it can incorrectly return much more than one minute of logging. We've seen it return almost a gigabyte of log data!
Even though we also limit the data to a short snippet at the end of all that text, we have to wait for it to be collected, and when the system grabs too much, it can take a while to retrieve and then discard the extra stuff.
The end result of all this is that we only do it when copies fail, and we put up a modal sheet while it's going on.
And Also, Too
Previously, when users sent in a report, we only included the log information when they reported an "Error during copy". We were a bit too clever for our own good there, since people didn’t always choose the right issue type, and then we’d have to ask for the report to be sent in again. We now always attach the log when using “Send to Shirt Pocket”.
These are small things, I know, but they'll help me help you more quickly and efficiently, should you ever need support.
I Can't Quit You, Baby
There are still some issues with quit that we're aware of...we're working on them.
Various and Sundry
There has also been a bunch of polishing and fixing things at the margins, thanks to user reports from highly unusual configurations, but as before, things are working really well on the vast majority of systems, which we’re really happy about. It’s just kind of boring to write about how great things are working for most people!
So you get the point. And now you get the results. Download away!
Download SuperDuper! 3.0 B7
Workaround Turtle Wednesday, October 25, 2017
Any program of sufficient complexity ends up having to work around behaviors that are undesirable. That might be a usability issue caused by default framework behavior, due to the interaction model selected by the designer. Or it might be an OS issue that only shows up in some situations (the recent iOS calculator bug is a good example of that).
Most, though, don't have to deal with the huge variation of hardware, software, OS, etc that a program like SuperDuper! has to handle.
The vast majority of the beta cycle has been focused on getting coverage of as many systems as possible. With a broad range of different setups and configurations, we can then find issues in the way macOS 10.13 is dealing with those configurations, and try come up with workarounds so, when when we release the GA version of SuperDuper! 3.0, the broader user community will have a smooth experience.
A lot of these changes have been focused on attached volumes, incorrect state information being returned by macOS calls or tools in some configurations and states, and coming up with ways to prod and probe until macOS returns the correct data.
It can be challenging to do, since you don't want to break "working" setups, and any workarounds should only come into effect in situations where they're needed. That way, when the OS problems are fixed, everything continues to operate.
All of that is a longwinded way of saying, we're happy to release Beta 6 of SuperDuper! 3.0, which has even more workarounds for macOS issues, covering a broad variety of situations we've seen in the past week or so. (It's workarounds all the way down!)
The new beta should work better on every system, and it fixes a problem with the beta autoupdate mechanism as well...so the next release's autoupdate should work better.
Download away, and thanks!
Click to download SuperDuper! 3.0 B6
Fraternal Twins Monday, October 23, 2017
(I really wanted to embed the teaser trailer for Peter Greenaway's A Zed and Two Noughts above, but alas it's a tad NSFW. Really great movie, though.)
Content warning: some strong language is used in this post. Not without reason.
So, here's something that you might not expect me to say:
Because of the way APFS "file clones" work, no program operating at the file level, including SuperDuper!, can make an exact physical copy of every possible APFS volume.
That's right. There are cases where we can't make an exact copy of your APFS volume. And Time Machine can't either. Nothing can.
That doesn't mean the copy is bad! It just means it might not be as space efficient as the original.
Doomed! Doomed! (Well, maybe not so doomed.)
Remember back in this post where I talked about the demo where Craig showed how fast it was to copy a gigantic amount of data?
I explained back then it was because the files aren't being copied. Rather, APFS creates new directory entries for the files, but references the same data blocks. So nothing is copied, which is fast. This is documented in Apple's APFS Guide.
From the user's perspective, these are different files. They're not like hard linked files, where changing one copy changes the others (not that most users know what hard links are). As far as users are concerned, they're totally separate, even if, at the file system level, they share the same data.
In APFS, if one of the cloned files is changed, even by a single byte, that changed data 'splits off' from the rest, and the files are now physically, and not just logically, separate—some of the data blocks now have two copies: the original ones, and the modified ones.
This process continues as the files diverge further.
The amount of logical drive space taken by the copies is twice the original, of course. However, the amount of actual space taken is, effectively zero...until the files are changed. At which point the space taken is the original plus the number of modified blocks.
This is all handled for you by APFS. You don't really have to think about it.
Quantum Theory?
Until you do have to think about it.
Consider this case: you have a 1TB APFS drive, and three 333GB files, named A, B, and C. So the drive is nearly full.
You then create a folder, and copy the three files into that folder with Finder. Of course, you'd expect the copy to fail and the drive to fill...but it doesn't.
In fact, if you look at the volume's size with Get Info, you may be surprised to see it has the same amount of data on it as was there before you made the copies. But, if you look at Finder's size for the folder, you'll see you now have 2TB of data on a 1TB drive. It's like magic!
At least until you change one of the files.
But now, select those files and folders with Finder and try to copy them to another 1TB drive. What happens?
The drive fills.
A Shitty Analogy
You can't copy it to the same size drive! But why?
The reason is there's no (public) way to find out that two files are actually sharing the same data (they might even only be sharing some of the same data, as I explain above). So, when copied, the "clone" relationship is broken, as is the ten-pounds-of-shit-in-a-five-pound-bag magic. You now have a full ten pounds. It doesn't fit...so you end up covered in shit.
But What If You...
Yes, we know:
What if you kept track of checksums of every file on the drive, and then made "clones" for each file based on whether the files had the same data?
Leaving aside how ungodly slow that would be (think about trying to match ten million files to each other via checksums every time you copied), remember that cloning operates at a block level, where some blocks may be shared and some may not be. At a file level, it just won't work.
How about using hard links?
That won't work either: clones and hard links are not semantically equivalent at all, since changing one of the hard linked files would change all of them, by definition.
Just ask the file system!
While there are APIs to create clones, there's nothing there to find out whether two files are clones... and also, the shared data is at the block level, so still, no.
Time Machine does it!
Well, not really. Time Machine does seem to be able to determine if two files are clones (which I assume it's doing with private APIs, because I can't find any documented APIs to determine if two files are clones). When it backs up cloned files, it uses hard links to represent them (since HFS+ doesn't support clones, and Time Machine can only back up to HFS+ volumes), and when it restores, it checks to see if those files are clones (which it tracks in a special database), and restores them as clones to APFS...unless they're restored to an HFS+ volume, where all bets are off.
But even in the best case, restoring to APFS, when files get 'separated' when they're changed, again, only the part of the file that was changed is separate. The other blocks are still shared. So even though they've jumped through hoops to maintain the clone relationship, there are lots of cases where Time Machine's own copies will increase in size too, and it happens more and more as the files diverge further.
You guys are so smart, you figure it out! Why are you asking me?
Geez, don't get so defensive!
We're All in this Together
So, as you can see, given the low-level behavior, there's really no solution, even when you're Apple.
What does this mean for you? It means you can get in cases where data that fits on a source drive won't fit on a destination, even when the drives are exactly the same size.
To avoid problems, you need enough space to store the full logical size of the data (that is, with all the "clones" separated) when you copy, unless you're copying the entire container at a sector level.
We Good?
Again, this doesn't mean your backup isn't good! It is! It has all your data!
What it does mean is that the data isn't stored as efficiently on the backup. So, it might not fit on your drive when you back it up. And it also might not fit when you restore, if the backup ends up larger than the capacity of the source.
That's easy to check, and the solution is also pretty easy: have plenty of free space on your drives, folks. It's always been good advice, and given all this hidden behavior that happens with cloned files, it's even more important with APFS.
OK, back to the code mines...
Automatic Transmission Sunday, October 22, 2017
Good news: we've set things up on our update server so that the Beta version will now automatically tell you when there's a new beta ready, using our regular update mechanism.
Here's how it works:
- You "opt-in" to the Beta by installing one of the beta releases from the blog.
- The update server knows what versions are Beta versions. When you check for updates, and if you're running a Beta, it returns the current Beta, rather than the current production release.
- At the end of the Beta, we set the final "Beta Update" to the production release as shipped. Everyone with the Beta automatically updates to the production version, and future updates are normal, production updates.
- If you want to participate in a future Beta, you can do so by downloading and installing a Beta version, and the process repeats.
Hopefully this will make it easier for everyone to keep up with the current Beta releases.
Don't forget, though: if you're running schedules, you won't notice the updates unless you launch SuperDuper! manually... so, if you want to be sure, check for updates manually.
Thanks to all the testers—we really do appreciate your help.
Forward Into the Past! Tuesday, October 17, 2017
Executive Summary
Beta 5 is linked at the bottom of the post: we now copy Recovery volumes from both HFS+ and APFS sources to APFS, and "stash" recovery on HFS+ destinations for restoration to APFS if needed.
Details, Details!
Before the advent of APFS, volumes were rigid elements created by physically partitioning a drive, logically erecting barriers between fixed areas of storage. While in later versions of macOS those barriers could sometimes be moved by the command-line diskutil, that functionality was not exposed in the GUI Disk Utility until relatively recently, and was prone to failure.
Even then, adding, resizing and removing partitions was more convenient and accessible...but relatively fragile. Reliable, extensive partitioning (with a friendly interface) was only available in 3rd party tools like iPartition, because it was able to physically relocate data blocks, change partition schemes, etc. The inherent rigidity of the layout of HFS+, even after the introduction of the intermediate-layer CoreStorage setup, got in the way of reliable volume creation and resizing, making the process risky.
Casiotone Nation
The design of APFS changes and improves all of that. Volumes inside an APFS container aren’t defined by rigid barriers, and their storage doesn’t have to be contiguous. All of the volumes in a given APFS container are extremely flexible and share a common free storage pool managed by the container itself. Creating and deleting partitions is a simple and safe operation. There's no need to create images to try to maximize storage efficiency on a drive, or to store three backups on a given drive: you just add new partitions, and they do what you'd expect. Failure is quite rare and for typically obvious reasons.
The Past is Prologue
When Apple got rid of CDs and switched to Recovery it was, in many ways, a step back. Reliable, immediately accessible, archivable media was replaced by a hidden volume on a drive that could fail. Even though Internet Recovery, an EFI-based failsafe, provided a backstop, it took a long time (and required internet access) when things went really wrong.
Save for bootable encrypted volumes, though, the Recovery volume was a nice thing to have on a backup volume, but not a necessary one. While it wasn’t terribly challenging to copy a Recovery volume, creating the partition for it, given diskutil’s capabilities, was risky. And its contents were also undocumented, even if relatively consistent from release to release.
Given Apple could recreate the Recovery volume during a macOS reinstall (a time consuming but easy operation that put a fresh OS under existing applications and data), and the fact that it wasn't needed for startup or restore, we decided to take a more conservative, safer approach and not copy Recovery.
Not because we couldn’t. But because we didn’t think we should, given the risks involved.
#It Gets Better
The introduction of APFS allowed us to revisit that decision. Because its more flexible volume creation is low-impact, the risks inherent in adding and managing the Recovery volume itself are minimal. Recovery now has its own special, documented “Role” within the APFS container, and its contents follow the pattern established for Preboot. Even encryption is done differently: it's properly managed in Preboot, which can be created and updated by a documented system tool, provided by Apple, further ensuring proper operation and compatibility as Apple makes changes and modifies requirements.
After carefully evaluating the new support and determining there were minimal risks, we decided that we could safely copy and manage Recovery for APFS containers, whether copied from APFS or HFS+ sources. And so we do.
That means we still don't create a Recovery volume on an HFS+ volume for the reasons above...but we can copy from an HFS+ volume to an APFS volume and properly copy its recovery to APFS (since that's as safe as APFS to APFS).
If you're copying HFS+ or APFS to an HFS+ device, we still work when restoring to APFS: we automatically create a Recovery “stash” on an HFS+ volume, and can restore it to APFS when necessary.
Your Well-Earned Reward
While the details above are a bit complicated, the best part is that, as with most other aspects of SuperDuper!, there’s nothing you need to do. The details are handled for you. It just works.
In the end, that’s our goal, and our slogan: Heroic System Recovery for Mere Mortals. We hope you agree.
SuperDuper! 3.0 B5.1
Postscript
The above is the 2nd post of Beta 5 (I called it Beta 5.1 but the version is the same). The first Beta 5 had a bug in it that caused temporary folder cleanup to fail.
This got through regression because we had tested against a number of bootable volume cases without checking the startup volume on the High Sierra test system itself (as opposed to the thumdrives, etc, that we've got for the various disk cases we handle). We tend not to run that every time because the variations (Erase, Smart Update, etc) take much longer with a huge drive. Alas, the startup volume is a different case...and we missed it.
Needless to say, that case is now checked even though it's slow (vs only during "dogfood" daily-build backup runs).
Ah, public betas This kind of stuff is OK when it's all internal. Sorry about that!
The past week's been spent delving into some pretty obscure problems. Special thanks, right at the top, to Jan, who spent a lot of time running special code that fixed some of this stuff. Owe you a beer, Jan.
Also, Beta 4 is linked at the bottom of this post, so if you want to just go there and not read how we got there, well, you won't hurt my feelings. Much. >sniff<
Heading to Entebbe
We had a report from a user that blessing Thunderbolt wasn't working. The symptoms were exactly like the FireWire problem previously reported (see below), which really didn't make sense, given it'd act like a regular SATA device, so it was back to reading a bunch of bless code to try to figure out what was going on.
I think I've figured this one out and, unfortunately, it looks like a bug in bless, at least in one case: RAID volumes.
You may remember that there are special volumes in an APFS container that are used for various purposes. One, Preboot, is responsible for booting tasks. When you bless a regular APFS volume, you're also configuring the Preboot volume in the container to support boot.
Now, one Preboot volume supports all the potentially bootable volumes within a given APFS container (there can be any number of them).
bless, when looking for the Preboot volume, sometimes can't find it, even when it's there. When this situation occurs, if you look at the 'verbose' bless info, you'll see, just before it fails (this is an example from a real user):
Returning booter information dictionary:
<CFBasicHash 0x7f94e2d2e5b0 [0x7fffaa32d5b0]>{type = mutable dict, count = 3, entries =>
0 : <CFString 0x106669ad0 [0x7fffaa32d5b0]>{contents = "System Partitions"} = (
disk0s1,
disk2s1,
disk3s1
)
1 : <CFString 0x10666a2b0 [0x7fffaa32d5b0]>{contents = "Data Partitions"} = (
disk2s2,
disk3s2
)
2 : <CFString 0x10666a2d0 [0x7fffaa32d5b0]>{contents = "Auxiliary Partitions"} = (
disk2s3,
disk3s3
)
}
In this case, it's not seeing any preboot volume at all. But when we look at the output of diskutil, we can clearly see it's there, and has the right role:
+-- Container disk5 40B6CB66-CB84-4913-9D81-E99117C5118C
====================================================
APFS Container Reference: disk5
Capacity Ceiling (Size): 750079967232 B (750.1 GB)
Capacity In Use By Volumes: 720822272 B (720.8 MB) (0.1% used)
Capacity Available: 749359144960 B (749.4 GB) (99.9% free)
|
+-< Physical Store disk4 0A426235-14D4-4F80-A334-DBA686914922
| ---------------------------------------------------------
| APFS Physical Store Disk: disk4
| Size: 750079967232 B (750.1 GB)
|
+-> Volume disk5s1 EDEBF4F8-D55E-41A4-9B91-4C8284696EDA
| ---------------------------------------------------
| APFS Volume Disk (Role): disk5s1 (No specific role)
| Name: Backup Disk (Case-insensitive)
| Mount Point: /Volumes/Backup Disk
| Capacity Consumed: 933888 B (933.9 KB)
| Encrypted: No
|
+-> Volume disk5s2 F8301391-7F37-4827-8189-AF830BA3D59A
| ---------------------------------------------------
| APFS Volume Disk (Role): disk5s2 (Preboot)
| Name: Preboot (Case-insensitive)
| Mount Point: Not Mounted
| Capacity Consumed: 18489344 B (18.5 MB)
| Encrypted: No
|
+-> Volume disk5s3 A75B0F60-9626-4F96-9D94-5AD97155838F
| ---------------------------------------------------
| APFS Volume Disk (Role): disk5s3 (Recovery)
| Name: Recovery (Case-insensitive)
| Mount Point: Not Mounted
| Capacity Consumed: 517365760 B (517.4 MB)
| Encrypted: No
|
+-> Volume disk5s4 5B344BEC-B85B-4373-97D3-081CEA467854
---------------------------------------------------
APFS Volume Disk (Role): disk5s4 (VM)
Name: VM (Case-insensitive)
Mount Point: Not Mounted
Capacity Consumed: 20480 B (20.5 KB)
Encrypted: No
The code that's having problems is in BLCreateBooterInformationDictionary.c in Apple's Open Source bless project. After some additional investigation, it looks like, in this case, if the APFS container is on an Apple RAID, bless can't find the Preboot volume and doesn't properly set up the container.
I've got one user's specific drive on order so I can test in his exact configuration here.
Of course, this doesn't explain every case we've seen, but it at least we think we understand what causes this one.
Re-Fire the Main Course
I dug out a FireWire drive here and created an adapter centipede (USB-C to Thunderbolt, Thunderbolt to FireWire, FireWire to drive) and... I was able to successfully bless and boot from a FireWire drive hosting an APFS volume.
So, while there are some FireWire configurations that bless fails on, it's not a blanket failure. It doesn't look like it's only FireWire RAID drives (some weren't), either. So, we're still investigating.
At this point, I'd generally encourage you to use USB-3/USB-C/Thunderbolt drives for any Macs that support those standards. They're all faster than FW800, have a future (as much as any technology has a future), and work fine.
Connection Required?
We were getting weird intermittent errors on some user systems that, when correlated (an exhausting process, since you have to try to figure out the common elements between a bunch of totally random cases), made no sense: the situations where the copies would fail corresponded to a lack of internet access (whether due to proxies, down connections, down DNS, etc).
What's especially strange about that is that...apart from the version check (and resulting software update, if accepted), we don't access the network. And this was happening to these users at the end of the copy, during the bless action.
Long story short (and thanks to Chuck for running a bunch of tests for me), we use xpath to parse the XML returned by the -plist parameters to various tools (such as diskutil). And that XML has a DTD at the start of it that references apple.com - and xpath would try to fetch that DTD, fail, and return a blank result.
Surprisingly simple fix: delete that line from the XML. No more network access, proper result return, everything's happy.
Bold and Robust
Due to an extremely high level of coffee consumption, this new beta fixes those and a bunch of other things. So, enough reading about the details and time to get to downloading.
Thanks, again, for helping out during this process. It's great to see it's working well for almost everyone, and satisfying to be able to resolve problems for those reporting them. Have at the new release, and let us know what you find!
SuperDuper! 3.0 B4
Maybe This Was a Good Week to Stop Sniffing Glue!
Support has returned to a normal post-major-OS-release level, mostly (there's still a lot), so I've got a little time to talk about one of the reported problems that was, I think, of general interest. Generally nerdy interest, that is. But it gives you a little insight into what's happening behind the scenes as we make progress towards GA release.
My APFS Backup Drive Isn't Showing Up in the Boot Menu!
While rare, this problem also occurs with HFS+, and is usually due to a drive that isn't responding correctly at boot time. Working around the issue typically involves attaching the drive after you reach the Option+boot menu: that way, the system and drive get a little more time to talk, and all works out.
But, with APFS, we were seeing a number of users indicating that their drive wasn't ever showing up in the Option+Boot menu, even though the drive was in the Startup Disk Preference Pane, and the usual workarounds didn't work.
On top of that, if the user actually booted up from the drive (from Recovery, the Startup Disk Preference Pane, or whatever), the drive would show up in Option+Boot, even after an Erase-then-copy backup...and even after deleting the various special APFS Preboot, Recovery and VM partitions.
Wait, What? C'mon.
I know! But it's true! And so it took a while to get it to happen in-house. But now that I've figured it out...it makes sense.
Doveryai no Proveryai
Additional investigation showed that you didn't actually have to start up from the drive. You merely had to select it in the Startup Disk Preference Pane. You could then switch back to your original drive without booting, and the drive would now always show up in Option+boot.
Given that, my initial thought (after WTF?) was that there was a new security enhancement at play. Perhaps, with the new "3rd-party applications can't set the startup drive" behavior in mind, Apple had taken another step, forcing users to select a drive as a startup drive using the Startup Disk Preference Pane at least once before it would work from Option+boot.
That sort of made sense, except the drive remained bootable across systems, and so there was no actual protection. So that wasn't it.
Schizoid Embolism?
As I mentioned above, once I had a drive that "worked", it would always work, whether Smart Updated or Erase-then-copied. I could even erase the volume with Disk Utility (which makes sense, since that's what SuperDuper! is doing, after all), and it would continue to show up in Option+boot (once a backup was made, of course).
Every one of these tests would take quite a while. Even with a minimal macOS High Sierra install, a test copy from scratch takes about 15 minutes, so each cycle was pretty costly in terms of time.
But, over time, I found that if I turned on all devices in Disk Utility, and erased the drive rather than the volume, the bad behavior returned. So, clearly, this was an outside-the-volume issue, but it followed the disk regardless of system. And that could only mean one thing.
EFI.
Don't Touch Me There
If you're not building a Hackintosh, you never have to deal with EFI. And while it's made the news lately due to some security issues with older Mac versions, it's not something you ever really hear about.
Basically, EFI stands for Extensible Firmware Interface (currently it's actually UEFI, but most people still say EFI). As that name implies, it's sort of an operating system inside the BIOS that can do stuff like trusted boot, GUID/GPT partitioning, etc.
So, a device can supply programs that run in that environment when attached. And that stuff is stored in a hidden EFI partition on the drive.
For security reasons, normal applications can't touch EFI.
Openly #Blessed
Given that discovery, the next step was verifying that the Startup Disk Preference Pane was using bless to do its thing (it was), and then looking at all the files bless was reading and writing.
Sure enough, one of the files being read (although not written) was /usr/standalone/i386/apfs.efi, and its presence on the drive was not enough.
Time to hit the Open Source repository. (Which is super useful; thanks, Apple, for releasing this stuff, even if it's unbuildable and references private frameworks.)
Analyzing the code there showed that, indeed, bless was embedding an APFS driver into EFI using a private, privileged API that we couldn't (and wouldn't want to) use. Interestingly, it was being done during the processing of --setBoot, the option that actually makes a drive the current startup volume. So there we go!
Don't Do Me Like That (RIP TP)
Except SuperDuper! can't use --setBoot, because it gives an error: only Apple apps can use --setBoot.
Or can it?
The code that embeds apfs.efi into the container's EFI is actually outside the block that actually sets the current startup drive. Which means that action will occur, regardless of whether there's an error.
So, by using an option that generates an error, --setBoot, we can get the EFI modified as needed. Adding --nextonly helps to minimize any potential side effects, too, since that just sets up the next boot without making the selection permanent (and doesn't do it anyway, since doing that requires privileges we don't have).
And, indeed, that solves the problem.
Spock Would Not Be Pleased
I'd argue that embedding the apfs.efi into the container's EFI should be done during the regular bless --folder operation, since the drive really isn't fully blessed without it, but I'm sure Apple had a reason to do it this way, even though it seems...illogical.
But logical or not, the multi-day investigation resulted in a workable fix, which will be in the next Beta, and obviously in the final release of v3.0 as well.
Back to it. Have a good weekend.
